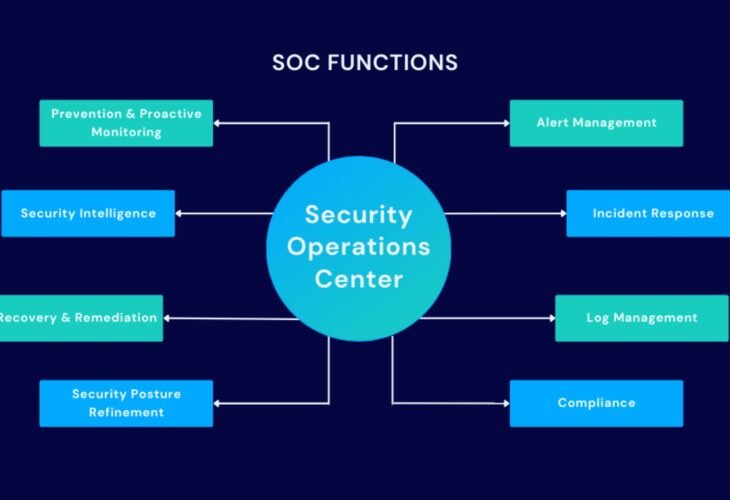
Security Operations Services are fundamental to maintaining a proactive and responsive security posture within an organization. These services involve the continuous monitoring, analysis, and management of an organization’s security environment to detect and respond to threats in real-time. By leveraging advanced technologies and expert insights, Security Operations Services ensure that potential security incidents are identified, investigated, and mitigated swiftly. This comprehensive approach helps safeguard critical assets, maintain operational continuity, and protect against evolving cyber threats.
Effective Security Operations encompass several key activities, including security monitoring, incident response, and threat intelligence. Security Operations Centers (SOCs) provide centralized oversight of an organization’s security landscape, utilizing sophisticated tools and technologies to monitor network traffic, analyze security logs, and detect anomalies. When potential threats are identified, Security Operations Services facilitate a structured incident response process to contain and resolve issues efficiently. This involves coordinating with various teams, conducting forensic investigations, and implementing remediation measures to prevent future occurrences.
In addition to reactive measures, Security Operations Services also focus on proactive strategies to enhance overall security resilience. This includes regular security assessments, vulnerability management, and the development of comprehensive security policies and procedures. By continuously evaluating and refining security practices, organizations can adapt to new threats and maintain a robust defense posture. Security Operations Services also provide ongoing training and awareness programs to ensure that staff are informed about the latest security practices and emerging threats. This holistic approach to security operations not only protects against immediate risks but also strengthens the organization’s overall security framework, enabling it to navigate an increasingly complex threat landscape with confidence.
